Four hackable devices I have bought in 2020: from a scientific calculator to a smartphone
As a technology writer and a fulltime nerd I like to tinker with everything, including all my hardware. I like to study it, program it, change it, let it do things that the manufacturer even hasn't thought about. I want to be in control.
Many of the articles and books that I write have this practical approach. And when I review hardware for a magazine and I find that the hardware has a cloud-based and a local mode, I turn my attention to the latter, because I don't have any interest in the former and almost all other reviewers will rave about the cloud-based mode anyway.
It won't surprise you that I love hackable hardware. Not hackable in the sense that it's insecure, but hackable in the sense that I can tinker with it. [1] In principle all devices are hackable, they just differ in the proficiency you need to do it. But this year I decided to put my money where my mouth is and buy some devices that are more or less expressly designed to tinker with. This way I want to support these companies, and of course it makes tinkering with these devices much easier for me, as I'm not an elite hardware hacker.
These are four hackable devices that I have bought in 2020 and that I really like:
NumWorks, a scientific calculator with MicroPython

As a math geek, I made do with the bc command or an interactive Python session on my computer when I needed to compute something, but it always felt a bit like... a hack? So I wanted a dedicated scientific calculator. I didn't find the one I had to buy when I was an engineering student, and I'm actually happy that I haven't found it, because I remember this device was quite kludgy.
Enter the NumWorks: at first sight it looks like the hipster's version of a graphical calculator, but the internals are as cool as its design. Both the hardware design and the software are available under a Creative Commons license. The 3D models of the case, the source code of the firmware, even the electronic schematics of the printed circuit board, you'll find it all on the company's Engineering page.
I have used the NumWorks a lot in the last few months and it's a dream to work with. Contrary to many hackable devices, it just works. It's slim and light, it has an amazing battery life, it instantly turns on and off, you can recharge it from a standard USB port and you can upgrade its firmware from your browser (for now sadly only Chromium/Chrome) thanks to WebUSB. It has all the basic computing and graphing functionality I need, and you can even run your own MicroPython scripts.
Another really cool feature is the online simulator of the NumWorks. This is a fully working version of the firmware that you can try in your web browser to explore the calculator's functionality. I hope more companies will offer something like this so you can try their device before you buy it.
PinePhone, a Linux phone designed for hackers
I have never liked the dumbed-down, closed walled gardens of Android and iOS with their ecosystem of apps that spy on you, yell at you with ads, force you to use their cloud service, and artificially limit what you can do with your phone. When you're running Linux on your desktop/laptop as I do, the contrast with the mature, privacy-friendly and open ecosystem of Linux is just unbelievable.
When I had to choose between Android and iOS for my first smartphone, the former seemed the lesser evil, so that's what I still use on my phone. But naturally I wanted to have a hackable phone with an operating system that treats me like an adult, and PINE64's PinePhone is the ultimate hackable phone. PINE64 has published as much information as possible to hack on the device, such as electronic schematics and data sheets.
You can run many Linux distributions on the PinePhone, and you have full control over your phone in a familiar Linux environment. Moreover, you have access to the vast ecosystem of open source programs that you're used to on the desktop.
That said, I don't consider the PinePhone ready as a daily phone. The hardware specifications are meager, the software is still buggy and many programs still have to be adapted to the mobile form factor. I'm using the PinePhone mainly as a development system to explore the mobile Linux ecosystem. [2]
But I like the vibe of the community of hackers that has originated around the PinePhone. And the device is really designed for hackers. There are six pogo pins on the back that expose an interrupt line, power input to charge the battery, a power source and an I²C interface. PINE64 has already announced a battery extension backcover and a keyboard backcover that make use of these pogo pins, but you're free to connect anything you want. There's a breakout board for easier access to the pins, and Martijn Braam even connected a thermal camera to the backcover of his PinePhone.
Kobol Helios64, a five-bay NAS with built-in battery
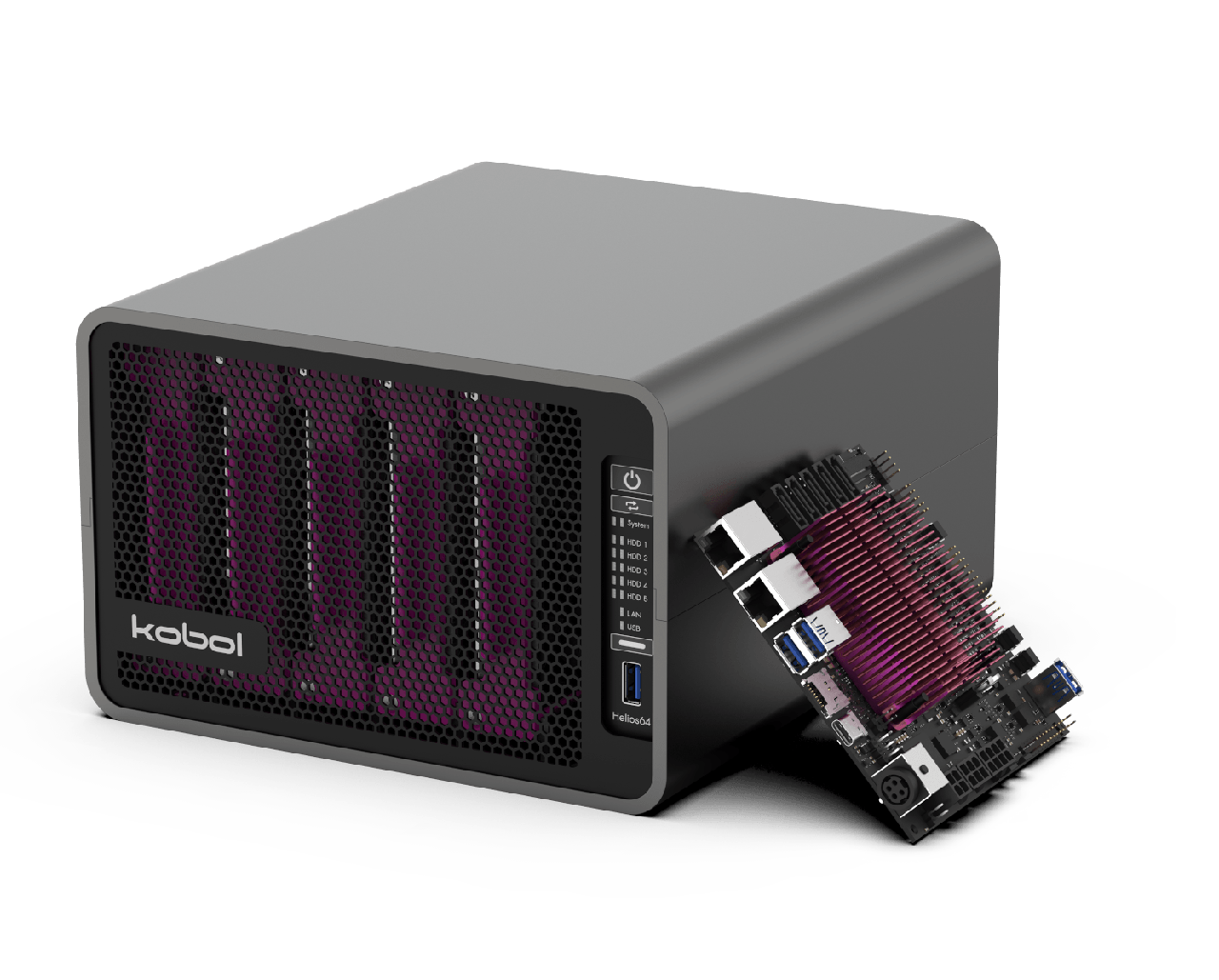
Linux is no stranger to NAS devices as an operating system, but most of them are locked down. Of course you can install a Linux-based or FreeBSD-based operating system on a server to function as a NAS [3], but just as for my other devices I wanted to have a NAS that was expressly designed for running your own Linux distribution and being hacked on.
That's how I discovered Kobol's Helios64. It's a quite well-looking five-bay NAS, powered by a 64-bit ARM Rockchip RK3399 SoC with 4 GB RAM, 16 GB eMMC for storage, dual Ethernet and a built-in battery.
The Helios64 comes as a DIY kit: you have to assemble it yourself, which took me two hours earlier this week. The advantage is that you learn a lot about the internals of your NAS while assembling it, which could come in handy when you start hacking on it.
Kobol's wiki has extensive documentation about the hardware, including electronic schematics and data sheets. The NAS has rich expansion possibilities through I²C, SPI, GPIO, ... for instance if you want to add a custom control panel or OLED display. Unfortunately the Kobol team has made a mistake in their Ethernet wiring, so the 2.5 Gbps Ethernet interface can not be connected to a Gigabit Ethernet switch without sacrificing performance, but they fully explain the fix and even suggest a hardware fix you can apply yourself.
Armbian has support for the Helios64, both in the Debian Buster and Ubuntu Focal variants. Not all hardware features are supported yet (for instance there are some issues with the USB Type C port in the driver), but I'm looking forward to testing the Helios64 with Armbian as a NAS.
reMarkable 2, a paper tablet with an awesome community
The reMarkable 2 is really what it says: remarkable. The company calls it a "paper tablet", I would call it an e-reader. I bought it mainly because I wanted to read PDF reports and data sheets, which I don't like to read on a computer screen and I don't want to print them either. I already owned a 6" Kobo e-reader, but I haven't used it in the last few years because it was too slow, too small and just too cumbersome.
The reMarkable 2 is everything you would want from an e-reader: a sharp 10.3 inch e-paper display, thin, light, fast and beautiful to the eye. You can also take notes directly on PDF files, which I have been using quite a lot in the week that I own the device now. And many people are even using their reMarkable 2 for drawing.
The company expects you to use their reMarkable cloud, which offers synchronization of your documents and notes and adds conversion of your handwriting to text. However, I want to self-host as much as possible, so before I bought the device I made sure that I could do without the cloud.
And yes you can. The reMarkable 2 is running a proprietary Linux system, Codex, but the company doesn't restrict you in any way. You have root access and you can run your own software on it. There's a wiki with many hacking tips, and the reHackable community on GitHub offers custom software and the Awesome reMarkable list of third-party software.
There's also a community-maintained repository of free software for the reMarkable, toltec, which works on top of the opkg package manager and the Entware distribution, and one of the projects that I'm definitely going to try is rmfakecloud, which fakes the cloud synchronization protocol of reMarkable so you can run this on your own server. The stock firmware of the reMarkable 2 has only quite basic functionality compared to some competitors, but I'm quite confident the open source community will expand the possibilities.
The reMarkable 2 also has pogo pins, and someone even used these to attach a foot pedal so he could move forward and back through sheet music while playing his instrument. So while not open source, the reMarkable 2 is quite hackable and I expect I will enjoy it a lot.